TITLE
Workaround instructions to address CVE-2021-44228 in Tanzu GemFire for VMs
ISSUE
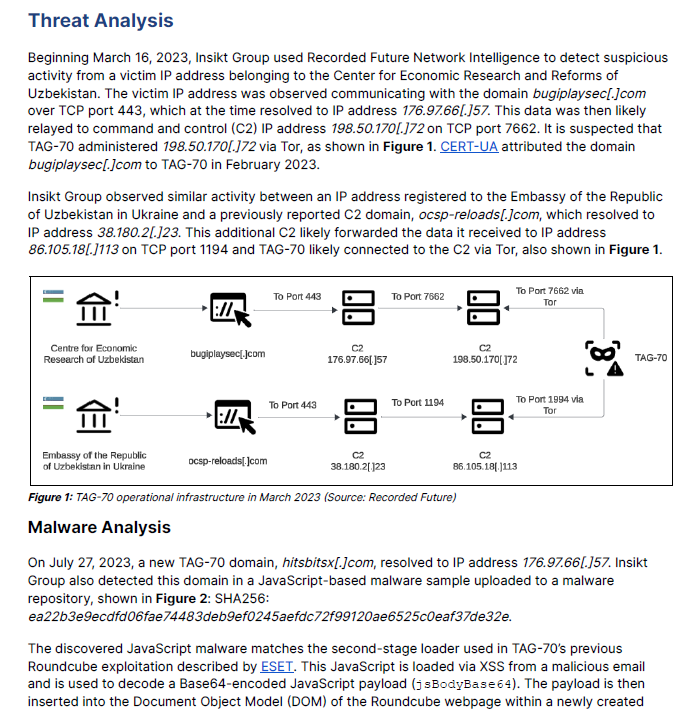
A critical vulnerability in Apache Log4j identified by CVE-2021-44228 has been disclosed that may allow for remote code execution. VMware has classified this issue as critical and is prioritizing publishing fixes and workarounds.
CVE-2021-44228 has been determined to impact Tanzu GemFire for VMs (all versions) via the Apache Log4j open source component it ships.
This vulnerability and its impact on VMware products are documented in the following VMware Security Advisory (VMSA). Review VMware Response to CVE-2021-44228: Apache Log4j Remote Code Execution (87068) before continuing.
CVE-2021-44228 has been determined to impact Tanzu GemFire for VMs (all versions) via the Apache Log4j open source component it ships.
This vulnerability and its impact on VMware products are documented in the following VMware Security Advisory (VMSA). Review VMware Response to CVE-2021-44228: Apache Log4j Remote Code Execution (87068) before continuing.
RESOLUTION
What actions can the reader take to resolve or work around the described problem?
IMPORTANT UPDATE (December 15, 2021)
We have recently discovered that the log4j2.formatMsgNoLookups=true workaround will NOT sufficiently protect against all currently know vulnerabilities.
As you may be aware, another CVE-2021-45046 has been discovered against log4j 2.15. We are now going to be releasing a new product on supported versions incorporating log4j 2.16 to eliminate all known vulnerabilities.