In a sophisticated cyber espionage operation, threat actors with connections to Belarus and Russia, identified as Winter Vivern—also known as TA473 and UAC0114—have launched a series of attacks exploiting vulnerabilities in Roundcube webmail servers. This campaign has impacted more than 80 organizations across Georgia, Poland, and Ukraine. The cybersecurity intelligence firm Recorded Future, referring to this group as Threat Activity Group 70 (TAG-70), has uncovered the extent of these breaches, marking a significant concern for European cybersecurity.
Direct download of the detailed analysis Russia-Aligned TAG-70 PDF report:
Exploitation of Roundcube Vulnerabilities: A Persistent Threat
The security flaws in Roundcube webmail servers have been a gateway for Winter Vivern's espionage activities, a tactic that ESET first brought to light in October 2023. This strategy aligns Winter Vivern with other Russia-associated cyber threat groups such as APT28, APT29, and Sandworm, all notorious for their attacks on email communication infrastructures.
Zimbra Email Software Compromise
Further demonstrating their capability, Winter Vivern successfully exploited a previously patched vulnerability in Zimbra Collaboration email software to penetrate organizations in Moldova and Tunisia in July 2023. This activity underlines the group's ongoing efforts to infiltrate and gather intelligence from various countries, reflecting a broader pattern of geopolitical espionage.
Scope and Objectives of the Cyber Espionage Campaign
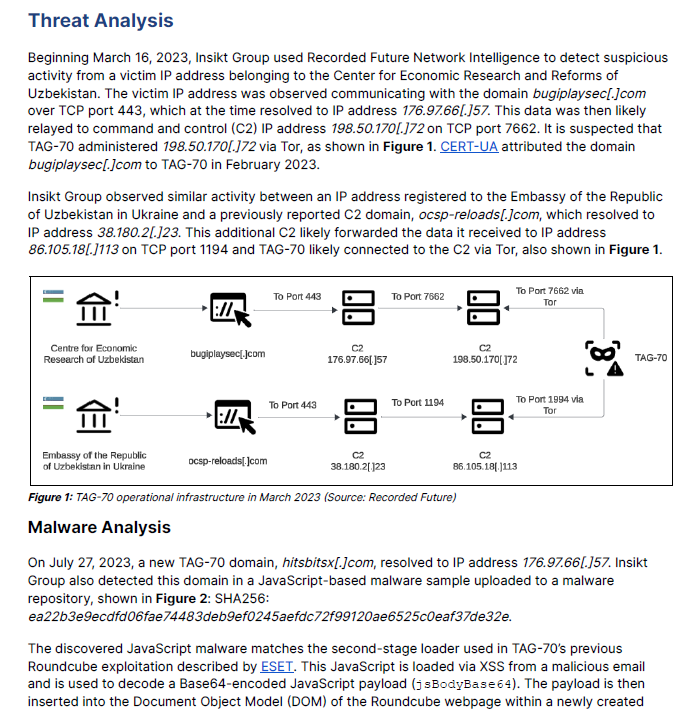
Recorded Future's investigation reveals that the campaign initiated in early October 2023, with the primary aim of surveilling European political and military strategies. This operation coincides with TAG-70's additional cyber attacks against the Uzbekistan government's mail servers detected earlier in March 2023.
The level of sophistication in TAG-70's attack methodologies is evident through their use of social engineering and exploitation of XSS vulnerabilities in Roundcube to bypass governmental and military defenses. These attacks are structured to exfiltrate user credentials to a controlled server, highlighting a well-orchestrated approach to cyber espionage.
Broader Geopolitical Implications
The targeting extends beyond European borders, with Recorded Future also identifying TAG-70's interest in Iranian diplomatic activities. The espionage against Iranian embassies in Russia, the Netherlands, and the Georgian Embassy in Sweden illustrates the group's broader geopolitical objectives, including insights into Iran's support for Russia and Georgia's aspirations towards EU and NATO membership.
A Call for Enhanced Cybersecurity Measures
This revelation of TAG-70's activities serves as a critical reminder of the ongoing cyber threats facing nations and organizations. The exploitation of Roundcube and Zimbra email vulnerabilities underscores the necessity for continuous vigilance and the strengthening of cybersecurity defenses to protect against such sophisticated espionage tactics.
By focusing on the specific threat actors, their methodologies, and the geopolitical context of their activities, this article aims to provide a comprehensive overview for cybersecurity professionals and interested readers, enhancing awareness and preparedness against cyber espionage campaigns.