VMware vSphere encompasses several distinct products and technologies that work together to provide a complete infrastructure for virtualization. The attackers have used certain commands in the shell script to modify the vSphere service in order to run the Xmrig miner. The shell script also contains the command to download a user mode rootkit from the attacker’s web server that was possibly used to hide the malicious acts.
Shell Script
The shell script (hash: b46764c046e0db26e6f43f46364ac0acad173541e7134611cb64e091db7b7ced) in this mining campaign starts with setting the SELINUX mode to permissive. This disables SELinux temporarily using setenforce 0 2>/dev/null command
(see Figure 1)
The shell script also contains commands which download the miner, the config file and the user mode rootkit from the attacker's web server. The attackers used wget utility to fetch the malicious components and chmod utility to make the components executable.
The rootkit gets saved as libload.so and gets run with the ld_preload environment variable
(see Figure 2)
The commands in the script then modify the vsphere service in the way to run the Xmrig miner as shown below
(see Figure 3)
After service modification, the commands in the shell script reload the services(daemon) so that the miner process could be started
(see Figure 4).
The Commands used are:
systemctl daemon-reload
systemctl enable vsphereui.service
systemctl enable vsphere.service
systemctl start vsphere.service
The mining operation is carried out using the wallet ID of the attacker “87ftP3g5Aa8BVWvfi4NQpSiSw4qYNvQm1CpUK2YpGxBoTwUA2S2GUE1NsiKUGP9pBrB6RDrKWTLKz11bXK5fsGhBSNMsUx9” over the pool gulf.moneroocean[.]stream:443.
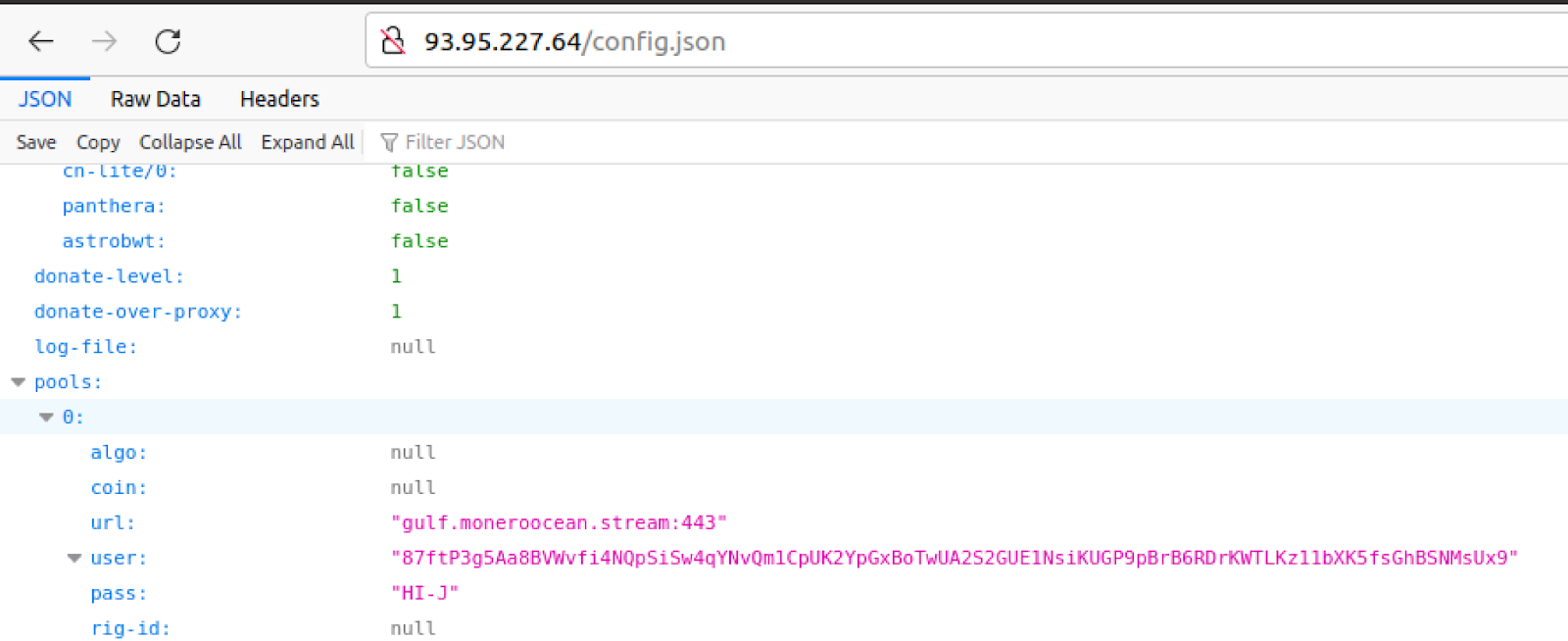
At the time of writing, according to moneroocean[.]stream, the user was paid 8.942 XMR.
Rootkit
The attackers also used the open source processhider rootkit for hiding the process . The processhider traverses the /proc filesystem in order to find the given process(in this case ‘crosbow’) and later hides the same.
(see Figure 6)
Conclusion
Cryptojacking campaigns mostly target the systems having high end resources. In this campaign as we saw the attackers tried to register the xmrig miner itself as a service(daemon) which runs whenever the system gets rebooted. In the past we have seen highly sophisticated groups targeting vulnerable Vmware services. Hence it becomes really important to monitor the suspicious processes, events, and network traffic spawned on the execution of any untrusted shell script.
EDR Detections
The malicious activities of the shell script and also identifies the malicious IP used in this campaign with a threat score of 10/10.
(see Figure 7&8)
IOCs
b46764c046e0db26e6f43f46364ac0acad173541e7134611cb64e091db7b7ced shell script
44cb9c1e139a06a86442c92b596a653659132fbc92986a2f5338630c90200af1 shell script
acbb4f3f9a13845de0c1c23f06dcb554817e610318e57718e63ce6a57af4911c Xmrig miner
791ce0a733ccf19ddccda8fa4c748d804460c5f5c61d8a3cdc41a0620f469991 rootkit
93[.]95[.]227.64 Attackers web server
gulf[.]moneroocean[.]stream